In January 2023, Trend Micro Inc. ("Trend Micro") established CTOne as a wholly owned subsidiary.CTOne is a provider of cybersecurity solutions for 5G/local 5G, and like its parent company Trend Micro, CTOne has domestic and international offices and operates transnationally.
Compared to conventional mobile communications, 5G/local 5G will be used much more widely in industrial domains, such as in IoT (Internet of Things) and OT (control and operation systems), so new perspectives and measures will be required in cybersecurity.
What kind of cyber security is required for 5G/Local 5G? We spoke with two people who are at the forefront of CTOne's business promotion efforts to find out what users need to pay attention to and how to prepare for the safe use of 5G/Local 5G in various applications.

Mr. Koji Taniguchi
Trend Micro Inc.
Connected Business Promotion Division
Senior Specialist, Network Security Technology Group

Mr. Ryohei Uesaka
Trend Micro Inc.
Connected Business Promotion Division
Manager, Network Business Development Group
-----I understand that CTOne is a subsidiary of Trend Micro. What is the specific positioning of CTOne, including its relationship with the parent company?
CTOne is positioned as a 100% subsidiary of Trend Micro. Originally, the organization was an in-house venture of Trend Micro that was engaged in new business development. This organization has been responsible for overall new business development related to IoT and OT (Operational Technology). Focusing on wireless networks and technology, the communications infrastructure that will support future digital transformation, CTOne was established to provide new security solutions specifically for this area. Like Trend Micro, CTOne also operates transnationally, with sales offices in Japan, Taiwan, Spain, and Germany.
-----Besides CTOne, are there any other start-ups that have been born out of Trend Micro?
Yes, there are three IoT and OT related companies. The first-born is TXOne, a company that provides security in factories. The second son is VicOne, which was founded in June 2022 and provides security for automated vehicle operation. VicOne is the youngest member of the company and has defined a wide range of networks, including carrier networks, Wi-Fi, sXGP, and local 5G, with a particular strength in networks using carrier technology. Currently, CTOne is developing security solutions for companies that utilize carrier networks and local 5G networks. CTOne is also working on security for open RANs (O-RANs), which allow interconnection of devices from various vendors by opening up the specifications of wireless devices and other equipment.
-----New mobile communication environments such as 5G and local 5G are used in a wide range of applications, so what new threats are emerging in such environments?
With the generational shift in mobile communications from LTE to 5G, the communications infrastructure will evolve with new technologies such as high speed, high capacity, and low latency. In terms of cyber-attacks, they are evolving and becoming more sophisticated every day, regardless of the generation transition, and there will be security threats and vulnerabilities triggered by the new technologies. For example, fake base station like things called stingrays (IMSI catchers) are a security threat in both LTE and 5G.
On the other hand, from a local 5G perspective, we see three emerging issues that users should consider.
The first is the network environment of the equipment. Basically, local 5G equipment is deployed in an end-user's on-premise environment, but relatively often the communication path from there is through the company's IT or OT network to the Internet. In this configuration, the local 5G is also exposed to IT or OT-specific security threats, and the local 5G must also consider threats coming from or going to IT or OT.
Second, there is the perspective of device management. There is a difference between devices managed by internal IT and those operated in the local 5G environment, and there is a great concern that the IT department will lose control over local 5G devices, or so-called shadow IT. If this happens, we believe that device management separate from traditional IT department management will be required to deal with threats such as loss, theft, and unauthorized devices brought into the environment.
Third, there is the issue of the environment in which the devices are installed. Even in local 5G, devices that connect to the network use SIM cards for continuous authentication of the communication environment. However, it is difficult to assume that the SIM card of one's own smartphone could fall into the hands of someone else without being noticed. In local 5G, there are not only smartphones, but also many stationary devices such as fixed cameras, AGVs (unmanned guided vehicles), and sensor devices. It is relatively easy to imagine a malicious person secretly removing SIM cards from these devices, inserting them into their own smartphones, and then using those smartphones to attack the local 5G network, or even the company network.
-----Please outline what kind of security solutions CTOne provides for those threats.
CTOne offers TMMNS (Trend Micro Mobile Network Security powered by CTOne), a security solution for local 5G, in order to deploy and operate local 5G with confidence.
TMMNS provides countermeasures to the three aforementioned issues by combining two components: Endpoint Protection, which is mainly bundled with a dedicated SIM card for security, and Network Protection, which is deployed in the local 5G network. In addition to detecting and blocking security threats originating from IT and OT networks, it also detects and blocks communication with SIM card switching threats. In addition, it visualizes the operational status of each device and the security status of individual devices by utilizing a dashboard that manages devices that cannot be managed by the IT department.
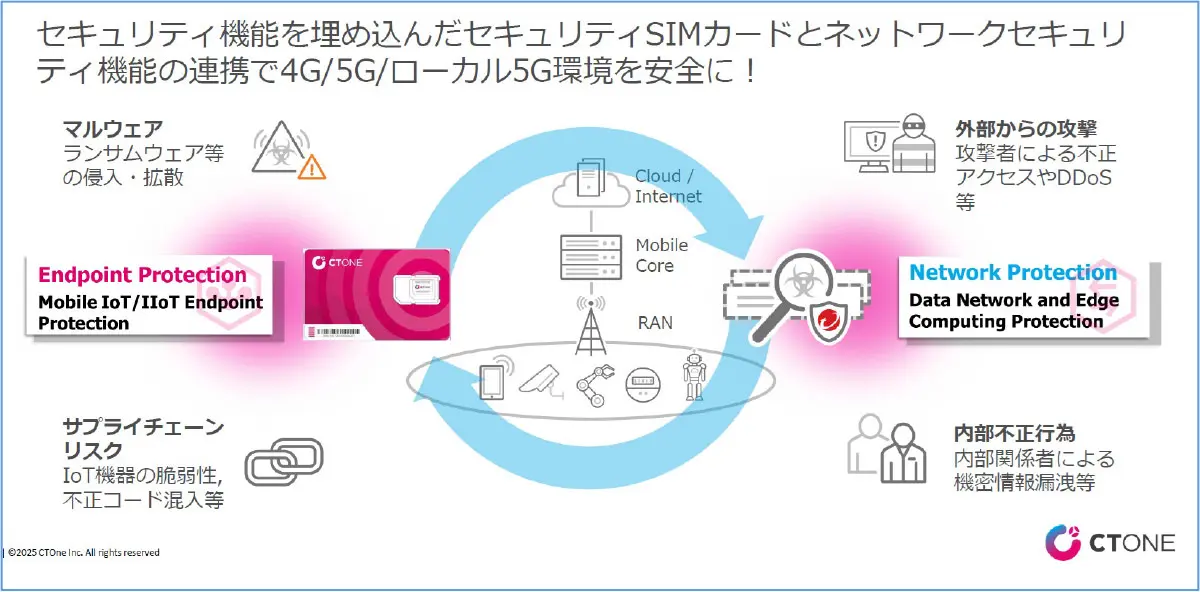
Figure 1: TMMNS security solution for local 5G
A key feature of CTOne's security solution is that security measures can be implemented simply by deploying a dedicated SIM card and Network Protection in the network. In addition, there is no need to modify local 5G devices or 5G software such as Mobile Core and RAN.
-----You mentioned that you will provide a dedicated SIM card. Is the dedicated SIM card the key tool for TMMNS?
For the security threats that originate from IT/OT or are directed at IT/OT, which were mentioned earlier in the network environment issue, Network Protection, not the SIM card, will monitor communications directly. If unauthorized communications that pose a threat from IT/OT flow into the local 5G network, those unauthorized communications can be blocked by Network Protection. Of course, if a local 5G device passes through the internal IT environment to the Internet, Network Protection can also block the threatening unauthorized communications.
The functionality with dedicated SIM cards is used in terms of device management as mentioned in the second item. Information from SIM cards of devices for local 5G is aggregated into a dashboard for centralized device management, including device connection status and security status.
Next, as a countermeasure against "spoofing" by SIM card replacement, if a legitimate device is unplugged and the SIM card is inserted into another device, Endpoint Protection can detect the change in the SIM card/device combination and automatically Endpoint Protection detects the change in the SIM card/device combination and automatically shuts down the wireless communication of the device.
One of the most frequently heard advantages of local 5G is the high level of security provided by the use of SIM cards, which are physical security. On the other hand, if the SIM card is stolen and misused, it can lead to new security threats (attack surfaces). As a countermeasure, Endpoint Protection with its dedicated SIM card increases the security strength of the device by blocking the local 5G connection with zero-trust security based on the authenticity of the device if the stolen SIM card is used in a device that is not under its control. Endpoint Protection enhances device security by blocking local 5G connections with zero-trust security based on device authenticity.
-----Does this mean that the dedicated SIM card/Endpoint Protection and Network Protection provide separate functions?
Yes, they can be used as independent functions. Each can be used as an independent function.
In addition, Endpoint Protection and Network Protection work together to provide a multilayered joint defense function for devices and networks. For example, Network Protection can be installed in two ways: IPS (Intrusion Prevention System), which is placed on the communication path, or IDS (Intrusion Detection System), which copies (mirrors) the communication and monitors it. IDS (Intrusion Detection System), which monitors communications by copying (mirroring) them. IDS monitors communications and detects but does not prevent unauthorized communications, while TMMNS, when detecting unauthorized communications using the IDS method, disconnects wireless communications to the SIM card of the device that is the source of the communication, thereby preventing further communications from that device. This prevents further unauthorized communications from the device and secondary damage such as internal spread to other devices.
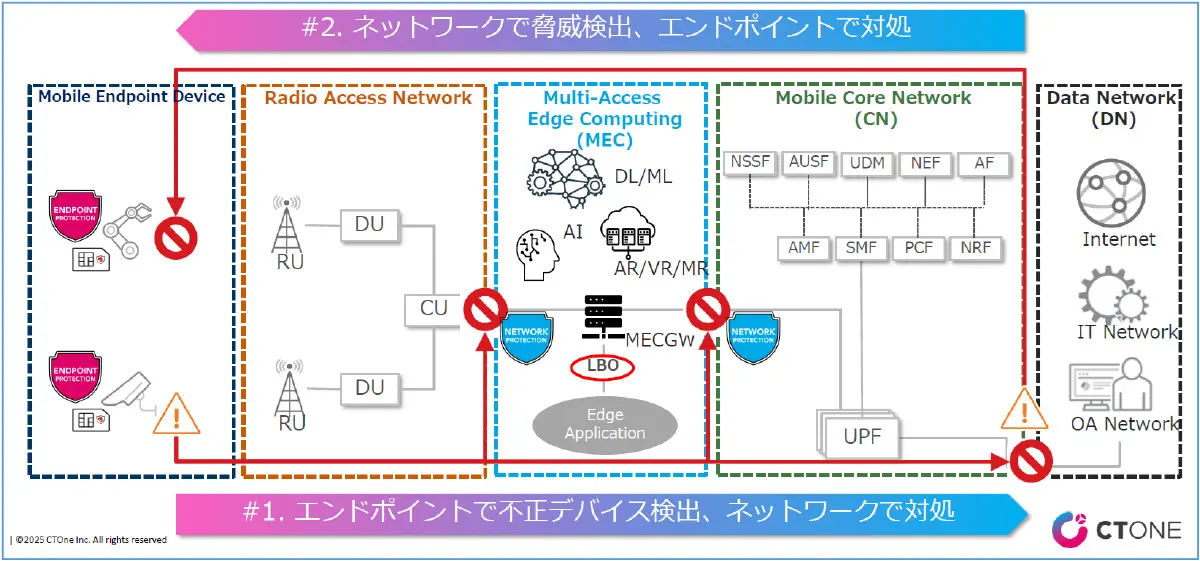
Figure 2: Multi-layered Defense by Endpoint Protection and Network Protection (Joint Defense)
-----Local 5G is a wireless network, what are the security difficulties compared to a wired network?
Compared to IT equipment connected to a conventional wired network, a wireless network allows more flexibility in where devices are installed, making it difficult to visually manage them. It is more difficult to know where the device is and who is using it than with a wired network, and it is impossible to disconnect the cable in case of a problem.
Local 5G is more secure than Wi-Fi because the SIM card is a strong authentication point. On the other hand, there are risks associated with SIM card replacement and the inability to manage devices that are shared between Wi-Fi and local 5G.
-----Does TMMNS have any restrictions on the types or models of devices it targets?
There are no restrictions or conditions that limit the target devices for the dedicated SIM cards used in TMMNS.
Apple devices are the first to support local 5G and support the Subscription Concealed Identifier (SUCI), which is an encrypted subscriber identifier. We have confirmed connectivity with many devices utilized in local 5G, including these Apple devices. We have a proven track record of using dedicated SIM cards for commercial operations as well.
For devices that have not yet been tested or will be sold in the future, we request that you perform a connectivity check with a dedicated SIM card in advance.
-----Local 5G is spreading in Japan. What is your assessment of the current state of cybersecurity awareness and response among local 5G end users? What are the particular areas that require improvement in the future?
Currently, local 5G is being used in energy-related plants such as electric power and gas plants, and in the transportation industry such as railroads, where vast sites are a prerequisite. There is a great need for local 5G in environments that require stable wireless communication, which is difficult to install with wired lines due to the large premises.
We feel that many in such industries have a strong awareness of security, partly because they are responsible for social infrastructure. However, there are many users who have a sense that "because it is local 5G, it is safe," and as CTOne, we are sending out a message that "while local 5G is highly versatile and secure in terms of communication, there are security measures that must be taken by users themselves who operate local 5G, and we need to make sure that we make allowances for this. We are in the process of sending out a message saying, "It is necessary to make allowances for this. When we explain the importance of security for local 5G, we have the impression that many users understand the necessity.
-----When using local 5G, from a cybersecurity perspective, userslong vowel mark (usually only used in katakana)What kind of preparation is needed to
Local 5G is often used in OT environments, and it is necessary to recognize that the traditional cyber-attacks and risks apply to all of them. On top of that, especially in local 5G operations, it is still necessary to build an environment that can constantly check whether the device is really working as expected when considering that the device is going wireless, and this is a concept unique to local 5G.
Another concept often mentioned in the security industry is "security by default. However, this is no longer the case, and it is important to consider security measures and operations from the network requirements definition and design stage. In the event of a security incident, it is extremely important to immediately understand what is happening in your organization's environment and prepare countermeasures to deal with it. In other words, it is essential to prepare security measures in advance to protect your organization from the ever-increasing number of sophisticated cyber attacks, and to do this, it is necessary to visualize the status of devices in the local 5G environment.
-----Local 5G has vendors who build it and end users who use it for business and other purposes, but how are they each expected to handle it?
In 2022, the Local 5G Security Guidelines were published by ICT-ISAC. It defines 13 risks in local 5G and proposes security risks that should be addressed by both the vendor and the end user.
The assumption behind this is that vendors must be able to adequately address those security risks. Of course, local 5G technology has standardized specifications for addressing security risks. However, its implementation is vendor-dependent.
As for what measures should be taken on the end-user side, the guideline states that measures need to be taken on the device side. It is the end user, not the vendor, that prepares the device, and there may be cases where vulnerability countermeasures may not be sufficient. In addition, the possibility of not being able to notice signs of cyber-attacks or internal fraud increases, leading to increased damage and delays in post-response. Thus, it is assumed that the vulnerability of the device or the user of the device may become a weak point, leading to attack surfaces. Security measures for devices will be a major point of focus for end users.
It is a hurdle and costly for users to read the local 5G security guidelines thoroughly and take countermeasures due to technical knowledge of local 5G, etc. When preparing the RFP, include "create a system that complies with the local 5G security guidelines", CTOne believes that end-user education is also an important point.
-----What are your expectations and prospects for the Japanese mobile market and mobile industry in terms of local 5G expansion? What are your expectations and requests for XGMF?
For the expansion of local 5G, one thing that is important is to further lower the cost of equipment. I also have high expectations for the expansion of applications for each end-user who will deploy 5G. If we can clarify applications and use cases that cannot be realized with Wi-Fi and establish their superiority, we will see further expansion of local 5G.
In the critical infrastructure field, we feel that security is often considered at the same time as the introduction of local 5G. However, in industries other than critical infrastructure, security is often considered a cost, and is often a secondary consideration. I believe that the situation will change drastically if applications are created that require the introduction of local 5G in this case, but also require security at the same time.
If you think about "how much would be lost if a factory stopped for a day," the investment in network infrastructure costs and security will usually be more reasonable than that. The same is true for local 5G, and we need to encourage users to change their thinking in this way.
As news of damage caused by cyber attacks has been increasing, there is a natural tendency for users' awareness and thinking to change. The number of inquiries to Trend Micro has also increased, and we have the impression that many of the inquiries are about what to do after being victimized. In addition, in the IoT and OT domains, labor saving will become a keyword, and people will be thinking about how to operate factories unmanned. However, if something happens at a factory and there is no one on site to restore operations, the factory will stop. This is an extremely big risk for business continuity, so the ability to take measures in advance to prevent the spread of damage will be a very important point in the Japanese market. In this sense, rather than replacing existing factory networks with local 5G, we believe that local 5G will be introduced when new factories are built, against the backdrop of the major keyword of labor saving, and that security will become more important in this context.
As for expectations for the XGMF, since it is an organization with a very large number of members (over 90 companies), we would like to see the XGMF leverage its volume to promote the formulation of industry rules and de facto standards. In terms of security, we would like to see the establishment of industry-specific security guidelines for the mobile industry, the introduction of a badge system, and the promotion of security legislation to government agencies. We hope that these efforts will lead to the expansion of safe and secure mobile networks in Japan. We would be happy to assist you in the development of security guidelines if you contact us.
*This article was prepared as part of a project contracted by the Ministry of Internal Affairs and Communications.